phase 01
UNDERSTAND NEW REALITY
HEY, IT'S TIME TO WAKE UP!
Relax. No rush. A good understanding of the topic is like a good quality foundation for a house, many times in the future you will come back to these basics when you want to explain to anyone the importance of introducing cyber security in every company or even at every home.
Cyber Security
How much does it cost you?
Same as buying a car, it depends. I know you expected a different answer, but sometimes not having a car can cost you your life. I am here to help you understand where you are currently and what you need to be safe and meet the required legal standards such as the NIS2 directive in the European Union.
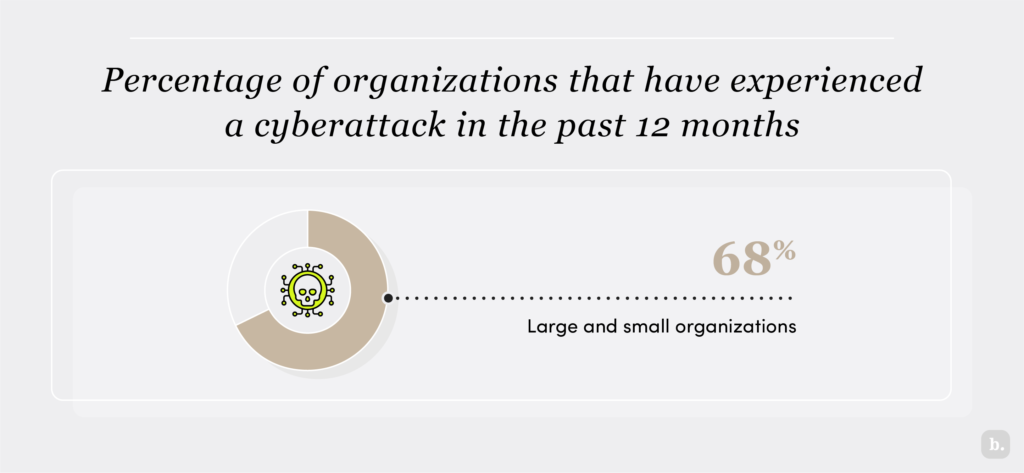
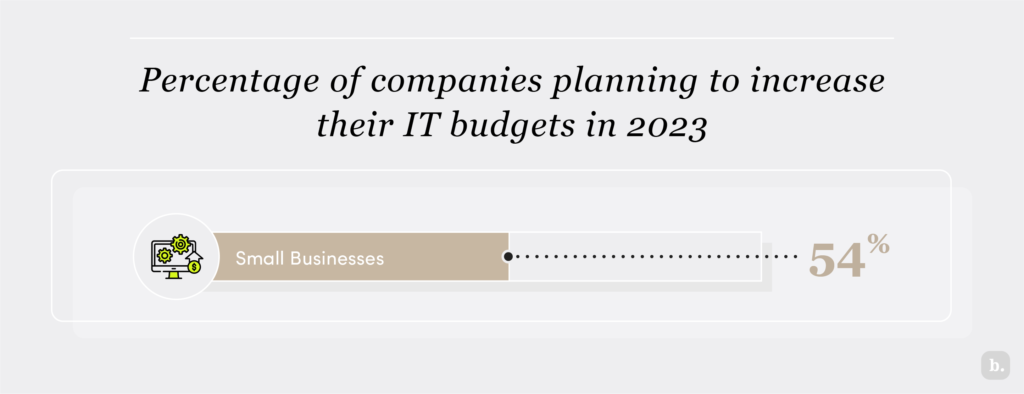
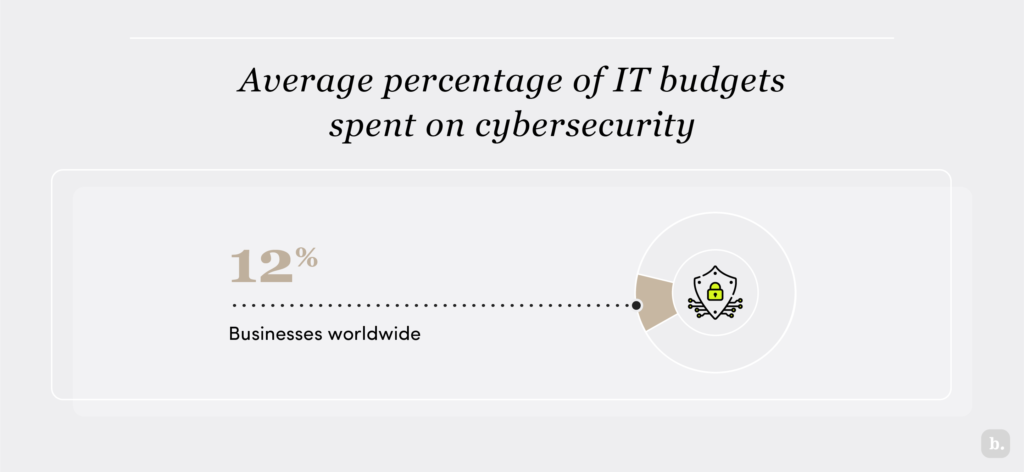
IBM’s 2023 Cost of a Data Breach Report
example the cost of
not good enough cyber security
Norsk Hydro
2019
The breach affect all 35,000 Norsk Hydro employees across 40 countries, locking the files on thousands of servers and PCs. The financial impact would eventually approach $71 million.
All of that damage had been set in motion three months earlier when one employee unknowingly opened an infected email from a trusted customer. That allowed hackers to invade the IT infrastructure and covertly plant their virus.Your Company in 2025
If you ignore NIS2, assuming maximum penatly from UE.phase 02
WHERE YOU HAVE TO BE?
ACCORDING TO NIS2
in progress
Your bussiness has to be compliant
At least at the level required by law. If you run a company in the European Union, you must make sure whether the NIS2 directive applies to you, and if so, to what extent. There's less and less time. Moreover, it is worth taking care of security in the company in a human way and conducting an audit that will show weak areas in our company. Prevention is better than cure.
NIS2 EU directive
The EU Directive NIS2 applies to a wider range of sectors and entities than its predecessor, aiming to enhance cybersecurity across the EU. It targets essential and important entities within critical sectors such as energy, transport, banking, financial market infrastructures, health, drinking water, wastewater, digital infrastructure, public administration, and space. Additionally, it covers providers of electronic communications networks or services, digital services like online marketplaces, online search engines, and social networking services platforms, and it introduces stricter supervisory measures, stringent enforcement requirements, and has broader incident reporting obligations.
Lorem ipsum headerum
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
phase 03
WHERE ARE YOU?
RELATED TO AUDIT
in progress
Lorem ipsum headerum
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
phase 04
WHERE YOU HAVE TO BE MINUS WHERE ARE YOU
= WHAT YOU NEED TO DO
= WHAT IS YOUR'S BUDGET ?
in progress
Dolor sit amet
Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Maturity level
MSS | Managed Security Service
TOOL | Product Name
phase 05
LET'S FIX IT
in progress